I was hacked for $12,000 of ETH today
Here’s a quick summary of what occurred to me within 24 hours:
- Once the attacker got access to Google auth (google authenticator, an app that provides a random number that I must enter to prove that it is really me doing something online), I was finished – this is why I prefer SMS auth over Google auth: the attacker would not have been able to view the authorization code on my local phone. But actually, even mobile phone numbers can be hacked and are generally considered a less secure form of authentication.
- How did he get access to Google auth? By adding a mobile phone to my google Account.
- How did he gain access to my google account? This is the big mystery. I think it is because my passwords are stored in LastPass and my lastpass was not locked down, meaning when I login to LastPass, I choose: authorize this computer for 30 days. I do this on my local machine, but I also did it on my VPS (a remote virtual private server). What this means is that anyone who logged into that remote machine had full access to LastPass without re-entering the Master Password… and that could’ve been anyone – an employee of the VPS company, a tech support staff from the people who help me with the VPS.
- Once he had access to my google account, he simply had to go to my google drive and search for “codes” and then enter a google backup code to add his device to my account… then instatnly everything in my Google account was pulled from the cloud into his mobile phone – my google drive, my google auth, my gmail, all of it. To someone in the Netherlands at that… why can’t I do an IP lock my google account and only allow devices to access it from specific IP numbers? But instead of complaining about what Google doesnt have, make it a point to put your backup codes outside of google so this doesnt happen again, given their current setup.
- A commentary on exchange security
- Kraken put a hold on suspicious ETH withdrawals from my account. It was easy to file a security ticket. It was harder to reach them by voice, but I did… but doing so required being able to login to the Kraken mobile app (they no longer accept phone calls) but the hacker changed my password on Kraken. But I managed to change it back and contact them by voice.
- Gemini happily processed withdrawals that should’ve thrown a red flag. Once I noticed some suspicious activity, I should’ve immediately been able to freeze the account and contact support. I also didnt get any warnings from Gemini about logins from new IP addresses.
- Crypto.com used to irritate me. Every withdrawal requires going through a “nagging” process of adding a wallet address and confirming the address by email and Google auth. Then you cannot use the new address for 24 hours. And they send you an email notifying you that a new address had been added. But all of this “nag” and “hassle” means that large amounts of funds cannot be sent to a new wallet (as did happen with Gemini – all he had to do was put his wallet address in and off went the funds without any due diligence).
But it gets even better
It just occurred to me that since I stored my seed phrases in Google drive that the person could open my web3 wallets once he found the seed phrases in Google Drive
- good bye to funds in the OK3 hot wallet
- good bye to funds in the Rabby hot wallet
and it was so easy once he got control of the Google profile, because Google Chrome automatically loads in all your plugins when you login to the Chrome profile. So all he had to do was open Google chrome and login using my google account and look at each wallet, then find the seed phrase in Google drive and type it in to activate the wallet – no 2FA confirmation or anything
I should’ve learned from my last 5-figure hack
About 5-10 years ago, I had a hot wallet on a VPS. The password to the VPS was “money1” – no, I am not proud of being this vulnerable. But facts are facts. All the hacker had to do was see where the wallets were with funds, once he had the IP of the wallets, then he attempted to login to the IP and the password was easily guessed. And 2 factor authentication did not exist then. So once he passed the 1 factor (password), nothing else was needed to take coins from all the hot wallets I had on the VPS… and Bitcoin was only $10,000 at that time. So that 5 figure hack is easily 6 figures or more now.
I should’ve listened to Decentralized Masters
I joined Decentralized Masters a few months back. They made it clear that large amounts of funds should be in your cold wallet, not in hot wallets on exchanges. At the time I said: “but I trust the centralized exchange more than myself” and the person replied: “we’ve been indoctrinated to trust an institution with our funds”
I learned how to use a cold wallet in Decentralized Masters, but had a “painful” amount of Bitcoin in a hot wallet
Everyone has a “burn” limit. Meaning you feel burned if you lose a certain amount of money on something. For me, the burn limit is about $500-1000. If I lose a grand or less, I dont feel so bad. But this $12,000 hack is 12 times larger than my burn limit. I’ve been burned.
Using a cold wallet is a bit laborious, but had all my non-burn money been there, I would not feel burned right now… But using the ledger wallet has issues too:
- did my wallet really come directly from Ledger? many people have lost their life savings by buying a ledger wallet on eBay. Because the person selling it knew the private key for the wallet and took all their funds after selling them the wallet.
- what if the Ledger wallet malfunctions? Well, Ledger has a reasonable monthly fee
I ignored Decentralized masters when they said to not store your seed phrase online
- all of the seed phrases for all hot and cold wallets were in google drive, nearly organized in a folder under my “Cryptocurrency” folder, all ready for the attacker to use.
Traditional exchanges have superior security
On a traditional exchange you cannot withdraw to a new bank account without going through a verification process. All this hacker did was copy his wallet address and paste it into Gemini and there goes $12,000! This would not have happened at crypto.com because you cannot withdraw to a new address immediately… At crypto.com you can only withdraw to vetted and verified addresses after 24 hours.
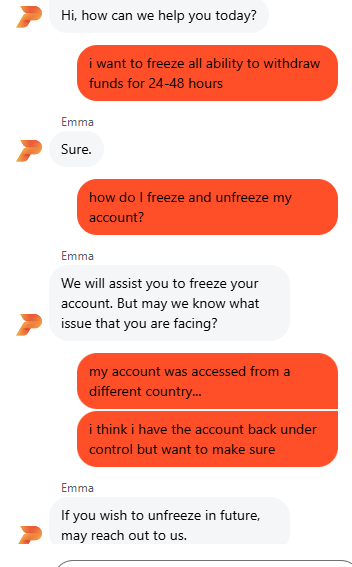
Freezing an account quickly – if you cannot freeze a hot wallet, then dont use that exchange:
Here you see me logging into Pionex and freezing my account in under 60 seconds
Passkeys are superior
Passkeys confirm identity via fingrprint or face recognition or another process that an attacker sitting elsewhere cannot imitate.
Defense wins ballgames
My online life with crypto and investing is all about offense – how to make more money as fast as possible. I never went through the steps of imagining that someone would steal from me and set up proper defenses against all possible attacks.
Demons are everywhere. The number of dependencies for safety is enormous
Once you start getting defensive, then you see demons everywhere. And everything that anyone does is grounsd for fear.
if I stop and think about all the ways this attack could occur, it might lead to me signing off the internet for good. I mean think about it:
- I am using a web browser that someone else made. Each web browser has a password manager feature. I use LastPass instead of the native password management of each browser.
- I have 10 or 20 web browser plugins, some crypto related, others not. But all made by people I dont know. If any of these browser plugins get infected with malware, then they might be able to eavesdrop/highjack the lastpass plugin.
- I have given remote access to my computer to tech reps using software like Teamviewer. But i am not sure that software is not still able to be used.
- My email address is available for 50 cents on the darkweb.
- If I move to Ledger then I have a private seed phrase of 12 words that I should not store online and should not share with anyone. This puts the full weight of money control on me… I want to use Ledger’s monthly service where they archive your seed phrase and protect your funds… but what if a Ledger employee commits an inside job
The Passkey demon
using a camera or fingerprint to verify myself is great.. but what if my camera is broken?!
The custodial service demon
Decentralized masters has a service called Legacy that they bill at a certain amount per month based on how much you have stored in their wallet.
Ledger also has a custodial service for a lower fee.
My fear is that decentralized master is a company of maybe 100 people and what if something happens to them? What happens to my legacy wallet?
I could have the same fear about Ledger, a much larger company but with whom i dont have a personal relationship. I can be on a zoom every week with the CEO of Decentralized Masters.
Cryptocurrency is private and confidential somewhat.
With cryptocurrency, my money can move from point A to point B without any barriers – no authorities confirming identity or validity. But with this freedom, come huge responsibility…. who can I report this theft to? the funds were withdrawn to a private and confidential wallet, not to a bank account registered in someone’s name.
But some people have been caught. And the one public things about crypto is the blockchain – all transactions are publicly viewable. So whenever the attacker moves the funds from this wallet, it is possible to follow each step.
ACTION STEPS TO A SECURE CRYPTO LIFE
- Prepare for locking crypto accounts if necessary. If there is no fast way to lock an account from withdrawals stay away.
- Move to passkeys
- Use physical 2FA instead of Google auth?
- When you must use Google auth, make sure that the biometric features are enabled. your phone must have a privacy screen in order that Google auth will require face recognition, fingerprint, pin or password
- Make sure to have in place backup procedures if physical 2FA gets lost/stolen/damaged
- Make LastPass harder to use – the default settings are slack. Go through all options and advanced options.
- Use a browser that locks itself – I use Wavebox. I’m pretty sure the attacker entered through my VPS and I did not have browser lock on any of the browsers there.
- Dont store your google account passwords anywhere. Memorize them.
I am either repressing anger or grateful for the lesson
if you drive in front of an 18-wheeler, you could suffer serious damage. In a way, this break-in was a good lesson before I suffered issues with larger amounts of capital.